Data leaks, application security and privacy. They are hot topics when we look at the headlines of the latest news. France asks Apple to turn off security features for a corona app. The Dutch corona app Covid19 Alert already has a data leak when uploading the source code and less than a month ago two hard drives with a backup of 6,9 million donor forms were lost.
Ensuring everyone's privacy sometimes seems difficult. The emergence of new smart technology makes it increasingly easier for hackers and malicious parties to obtain data*. Topics such as data security and privacy are becoming increasingly important.. and achieving them seems more difficult.
Yet there is not only bad news: with the arrival of new technology, software specialists and the tools they use are also getting smarter. User privacy and data security are spearheads when developing and maintaining an app. By using the latest techniques in application security, the privacy of the user can be guaranteed. In addition, many of these privacy violations can be prevented by working meticulously and pragmatically.
At Coffee IT we strive to offer the highest quality to our customers. Application security is an essential part of this. We ensure that apps are properly secured. In this article we provide important advice for data security in apps. How do you secure an app?
* We do not include the example of the two lost hard drives in this example. This was a human error and might have been prevented by using an app instead of hard drives.
Overview (reading time: 6 minutes)
What makes an app a well-secured app?
A well-secured app meets the set security standards. These standards are set at multiple levels: the EU, national, societal or in the Google Play Store and Apple App Store. Well-secured means that only authorized users have access to privacy-sensitive data. In addition, an app should never be misleading or unreliable.
As a company or app owner, securing an app is not an unnecessary luxury. If you want to avoid large fines and nasty PR issues, it is advisable to ensure that the app is properly secured. Is privacy-sensitive data collected in an app? In that case it is important to be aware of this. Both the consumer and the company have an important role to play in this. We can roughly divide app security into two categories:
- The minimum measures for privacy assurance and data security within apps
- Additional measures for data security in apps
Minimum measures for securing an app
The basic measures for securing important and privacy-sensitive data:
- Provide secure data traffic by only sending data with an encrypted connection. You do this through an SSL or HTTPS connection. By encrypting the data between sender and receiver, you prevent third parties from accessing this data*. Do you want to go one step further? Then add an SSL pinning or a TLS certificate (the successor to SSL). This prevents a so-called man-in-the-middle attack.
- Use only unique en strong passwords.
- encrypt en secure all data stored on a device.
- Always work with the latest software and operating system updates. Hackers or malicious parties often use older versions with problems to access systems and data. By consistently updating software, you reduce this risk.
- Which user is allowed to see which data? In other words: vshare the roles. Can this user only view data or also edit and even delete data? By dividing roles and identifying a user through a login (Facebook/Google/email) and linking it to a role, you secure the data. Take, for example, an app that we are currently developing for restaurants. We have divided this into three user roles: user, admin and owner. An owner user role can change content related to his own restaurant. An admin user role can change all data. A user can only log in to the app and leave reviews. By thinking carefully about the user roles, you protect the data within the app.
- Use layer security. This means that you provide security for every step where a hacker can enter. For convenience, compare this with a house. This is how you put a fence around your house and lock the doors with a lock.
* Did you know: nowadays it is very easy to get SSL certificates. We use for this 'let's encrypt'. Let's encrypt is a non-profit organization that encourages companies to make connections secure with HTTPS. They provide free SSL certificates, you used to have to pay for this.
Additional (recommended) measures for securing an app
If you want to go a step further, you can add some extra security layers to ensure user privacy and application security. With this you can think of:
- Awareness and attention of develop. Perhaps one of the most important aspects of developing well-secured apps. A structured, logical and clean code provides more security and overview. Security measures are maintained by applying the 'secure-coding' principles. This in turn ensures that the underlying infrastructure is properly implemented and misconfigurations and outdated software are prevented (the earlier point with basic application security)**.
- Continuous application security. By conducting consistent checks, it can be checked whether malicious parties can manipulate the underlying infrastructure, for example by entering or exchanging incorrect data. By doing this in iterations, security vulnerabilities are detected in a timely manner.
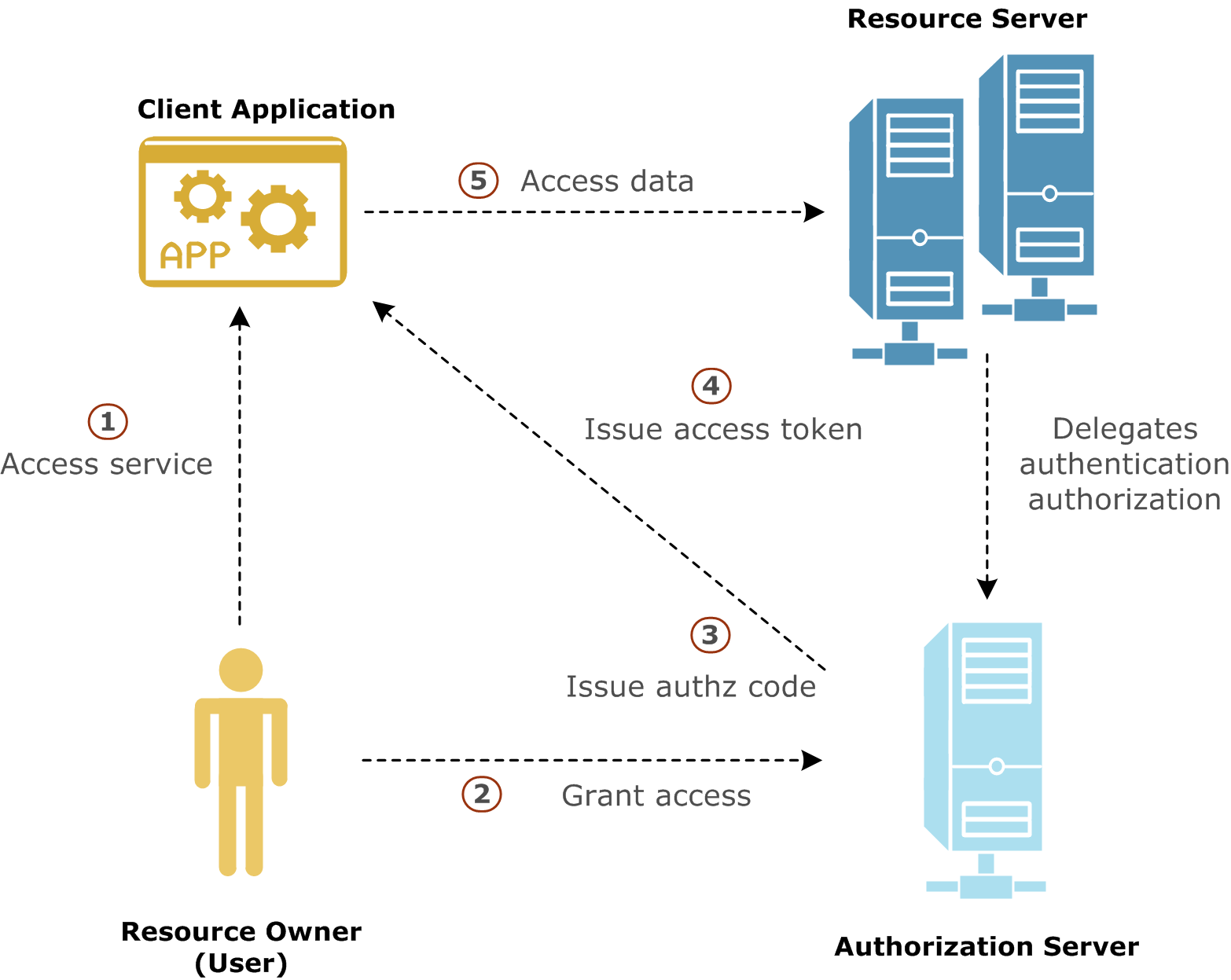
- Use OAuth 2.0. By using an OAuth workflow you give third parties secure access to the API or HTTP endpoints. This is not done via a login, but via an access code. The app then receives an access token after logging in, which is valid for a certain period of time. With that access token you can then retrieve data for a specific role (user/admin/owner etc.) for a certain period of time. The backend then checks which user is involved and whether they are allowed to access the data. See the image below for a schematic workflow of OAuth 2.0.
- The security of an app's backend should be nailed down. You can check this using the OWASP (Web Application Security Sheet).
** This often went wrong with the much-discussed corona apps. Security tests have shown that the 'secure coding' principles have not been applied sufficiently. For example, hard-coded passwords can be traced in the readable source code that has been published. This allows access to the databases and underlying infrastructure. In many cases, this infrastructure and API was not secured with identification and authentication.
Data protection by law
Fortunately, as consumers, we are also protected against data breaches by law. The AVG law is perhaps one of the most important new laws that protects the rights and privacy of app users. Organizations that do not handle customer data carefully can be fined. In addition, reporting a data breach has been mandatory since 2016. Every organization is obliged to report a data leak or security breach to the Dutch Data Protection Authority.
Safety first: attention to app privacy and data security
Securing data applies to every company. Which security measures apply differs per app. After all, apps are customization. In general, the rule of thumb applies: the more privacy-sensitive information the app contains, the heavier the security and protocols. Still, every app should have a certain basic level when it comes to application security.
The impact of poorly secured apps will only increase in the near future. After all, more and more information is being collected online, such as your geolocation, activity history or contact details. We therefore recommend that you think carefully about data security and identify the risks. By applying the above measures you ensure a level of security and privacy for app users. Of course there are many additional measures you can take for extra data security. Depending on the type of app, we can inform you about this. Do you want to know more about this or do you have other questions? contact us.